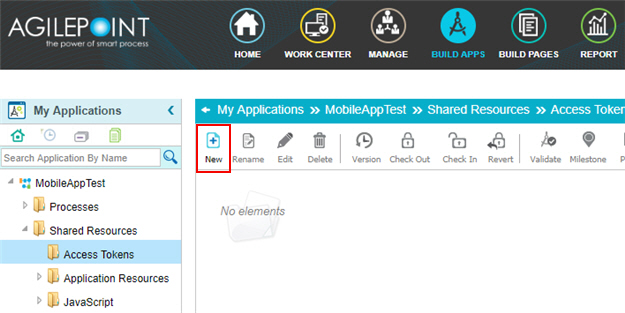
Access Token for Database
Configure an access token to connect to a database.
Background and Setup
Video: Configure Access Token for Trial SQL Server Database
Examples
Good to Know
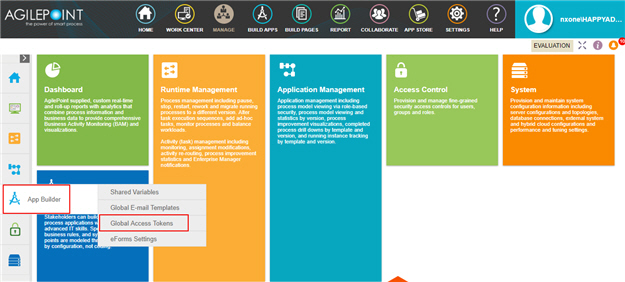
- In most cases, you can use a global access token or
an application level access token:
- Global access tokens are shared across all users and applications. If you want all process designers and runtime app users in your AgilePoint NX tenant to be able to connect to an external data source, use a global access token. An example is a SharePoint site on an intranet that all employees in a company can access.
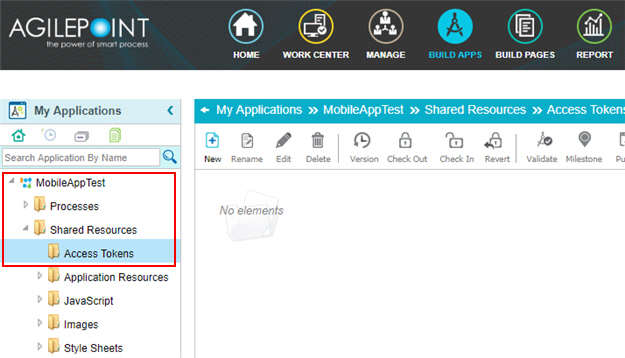
- Application level access tokens are shared with all processes in a process-based app, or restricted to use within a form-based app. Use application level access tokens if only process designers or runtime app users for a particular application should access an external system — for example, a Google Drive account that is only used to share files within a small team.
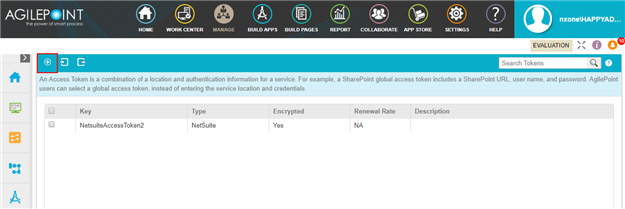
- Access tokens are collections of credentials that are used to authenticate communication directly between AgilePoint NX and an external system. Because it is the AgilePoint NX system that uses these credentials, rather than an app, there is no difference between
design time
and
runtime
access tokens. Access tokens are never checked in or published, and they do not use version control. If you change an access token in the App Builder or Manage Center, the access token changes immediately everywhere the access token is used. Changes to application level access tokens apply to all versions of an application, including running application instances. Changes to global access tokens apply everywhere they are used in AgilePoint NX. You can not roll back an access token to a previous version.
For more information, refer to What Data Is Deleted When I Delete an App or Application Resource?
- Some information about third-party integrations is outside the scope of the AgilePoint NX Product Documentation, and it is the responsibility of the vendors who create and maintain these technologies to provide this information. This includes specific business uses cases and examples; explanations for third-party concepts; details about the data models and input and output data formats for third-party technologies; and various types of IDs, URL patterns, connection string formats, and other technical information that is specific to the third-party technologies. For more information, refer to Where Can I Find Information and Examples for Third-Party Integrations?
How to Start
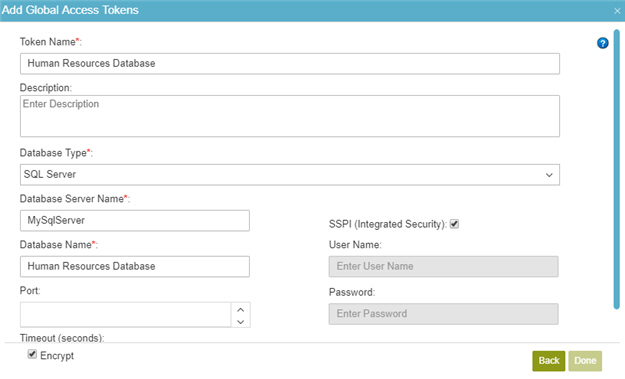
Fields
| Field Name | Definition |
|---|---|
|
Token Name |
|
Description |
|
|
Database Type |
|
|
Database Server Name |
|
|
Database Name |
|
|
Port |
|
|
Timeout(seconds) |
|
|
SSPI (Integrated Security) |
|
|
User Name |
|
|
Password |
|
|
Test Connection |
|
Encrypt |
|